-
容器编排学习(六)服务管理与用户权限管理
一 service管理
1 概述
- 容器化带来的问题
- 自动调度:在 Pod 创建之前,用户无法预知 Pod 所在的节点,以及 Pod的IP 地址
- 一个已经存在的 Pod 在运行过程中,如果出现故障,Pod也会在新的节点使用新的IP 进行部署
- 应用程序访问服务的时候,地址也不能经常变换
- 多个相同的 Pod 如何访问他们上面的服务
- Service 就是解决这些问题的方法
2 服务的自动感知
服务会创建一个 clusterIP 这个地址对应资源地址,不管pod 如何变化,服务总能找到对应的 Pod,且clusterIP保持不变
3 服务的负载均衡
如果服务后端对应多个 Pod,则会通过 IPTables/LVS 规则将访问的请求最终映射到 Pod 的容器内部,自动在多个容器间实现负载均衡
4 服务的自动发现
服务创建时会自动在内部 DNS 上注册域名
域名:<服务名称>.<名称空间>.svc.cluster.local
二 clusterIP 服务
1 概述
默认的 ServiceType,通过集群的内部 IP 暴露服务,选择该值时服务只能够在集群内部访问。

2 创建服务
- # 资源对象模板
- [root@master ~]# kubectl create service clusterip mysvc --tcp=80:80 --dry-run=client -o yaml
- [root@master ~]# vim mysvc.yaml
- ---
- kind: Service # 资源对象类型
- apiVersion: v1 # 版本
- metadata: # 元数据
- name: mysvc # 资源对象名称
- spec: # 详细信息
- type: ClusterIP # 服务类型
- selector: # 选择算符
- app: web # Pod标签
- ports: # 端口
- - protocol: TCP # 协议
- port: 80 # 监听的端口
- targetPort: 80 # 后端服务端口
- ********************************************
- selector:
- app: web # 引用标签
- ********************************************
3 域名自动注册
- [root@master ~]# kubectl apply -f mysvc.yaml
- service/mysvc created
- [root@master ~]# kubectl get service
- NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
- kubernetes ClusterIP 10.245.0.1 <none> 443/TCP 2d18h
- mysvc ClusterIP 10.245.5.18 <none> 80/TCP 8s
4 解析域名
- # 安装工具软件包
- [root@master ~]# dnf install -y bind-utils
- # 查看 DNS 服务地址
- [root@master ~]# kubectl -n kube-system get service kube-dns
- NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
- kube-dns ClusterIP 10.245.0.10 <none> 53/UDP,53/TCP,9153/TCP 3d10h
- # 域名解析测试
- [root@master ~]# host mysvc.default.svc.cluster.local 10.245.0.10
- Using domain server:
- Name: 10.245.0.10
- Address: 10.245.0.10#53
- Aliases:
- mysvc.default.svc.cluster.local has address 10.245.5.18
5 创建后端应用
- [root@master ~]# vim myweb.yaml
- ---
- kind: Pod
- apiVersion: v1
- metadata:
- name: web1
- labels:
- app: web # 服务靠标签寻找后端,定义标签
- spec:
- containers:
- - name: apache
- image: myos:httpd
6 服务自动感知
- [root@master ~]# kubectl apply -f myweb.yaml
- pod/web1 created
- [root@master ~]# curl http://10.245.5.18
- Welcome to The Apache.
7 服务的负载均衡
- [root@master ~]# sed 's,web1,web2,' myweb.yaml |kubectl apply -f -
- pod/web2 created
- [root@master ~]# sed 's,web1,web3,' myweb.yaml |kubectl apply -f -
- pod/web3 created
- [root@master ~]# curl -s http://10.245.5.18/info.php |grep php_host
- php_host: web1
- [root@master ~]# curl -s http://10.245.5.18/info.php |grep php_host
- php_host: web2
- [root@master ~]# curl -s http://10.245.5.18/info.php |grep php_host
- php_host: web3
8 服务的工作原理
-kube-proxy是在所有节点上运行的代理。可以实现简单的数据转发,可以设置更新 IPTables/LVS 规则,在服务创建时,还提供服务地址DNS自动注册与服务发现功能

9 使用服务固定IP
ClusterIP 是随机分配的,如果想使用固定IP,可以自定义,但 IP 的范围必须符合服务的 CIDR
- [root@master ~]# vim mysvc.yaml
- ---
- kind: Service
- apiVersion: v1
- metadata:
- name: mysvc
- spec:
- type: ClusterIP
- clusterIP: 10.245.1.80 # 可以设置 ClusterIP,固定IP
- selector:
- app: web
- ports:
- - protocol: TCP
- port: 80
- targetPort: 80
- [root@master ~]# kubectl delete service mysvc
- service "mysvc" deleted
- [root@master ~]# kubectl apply -f mysvc.yaml
- service/mysvc created
- [root@master ~]# kubectl get service
- NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
- kubernetes ClusterIP 10.245.0.1 <none> 443/TCP 2d18h
- mysvc ClusterIP 10.245.1.80 <none> 80/TCP 65s
端口别名
- [root@master ~]# kubectl delete pod --all
- pod "web1" deleted
- pod "web2" deleted
- pod "web3" deleted
- [root@master ~]# vim mysvc.yaml
- ---
- kind: Service
- apiVersion: v1
- metadata:
- name: mysvc
- spec:
- type: ClusterIP
- clusterIP: 10.245.1.80
- selector:
- app: web
- ports:
- - protocol: TCP
- port: 80
- targetPort: myhttp # 使用别名查找后端服务端口
- [root@master ~]# kubectl apply -f mysvc.yaml
- service/mysvc configured
- [root@master ~]# vim myweb.yaml
- ---
- kind: Pod
- apiVersion: v1
- metadata:
- name: web1
- labels:
- app: web
- spec:
- containers:
- - name: apache
- image: myos:httpd
- ports: # 配置端口规范
- - name: myhttp # 端口别名
- protocol: TCP # 协议
- containerPort: 80 # 端口号
- [root@master ~]# kubectl apply -f myweb.yaml
- pod/web1 created
- [root@master ~]# curl http://10.245.1.80
- Welcome to The Apache.
10 服务排错
服务 web123 的使用 web1作为后端,提供 Cluster IP 服务
- ---
- kind: Service
- apiVersion: v1
- metadata:
- name: web123
- spec:
- type: ClusterIP
- clusterIP: 192.168.1.88
- selector:
- app: apache
- ports:
- - protocol: TCP
- port: 80
- targetPort: web
三 对外发布应用
1 发布服务
clusterIP 服务可以解决集群内应用互访的问题,但外部的应用无法访问集群内的资源,某些应用需要访问集群内的资源,我们就需要对外发布服务
2 服务类型
- clusterIP:默认类型,可以实现 Pod的自动感知与负载均衡,是最核心的服务类型,但 clusterIP 不能对外发布服务,如果想对外发布服务可以使用 NodePort 或 Ingress
- NodePort:使用基于端口映射(默认值:30000-32767)的方式对外发布服务,可以发布任意服务 (四层)
- Ingress:使用Ingress 控制器(一般由 Nginx 或 HAProxy 构成)用来发布 http、https 服务 (七层)
四 nodePort 服务
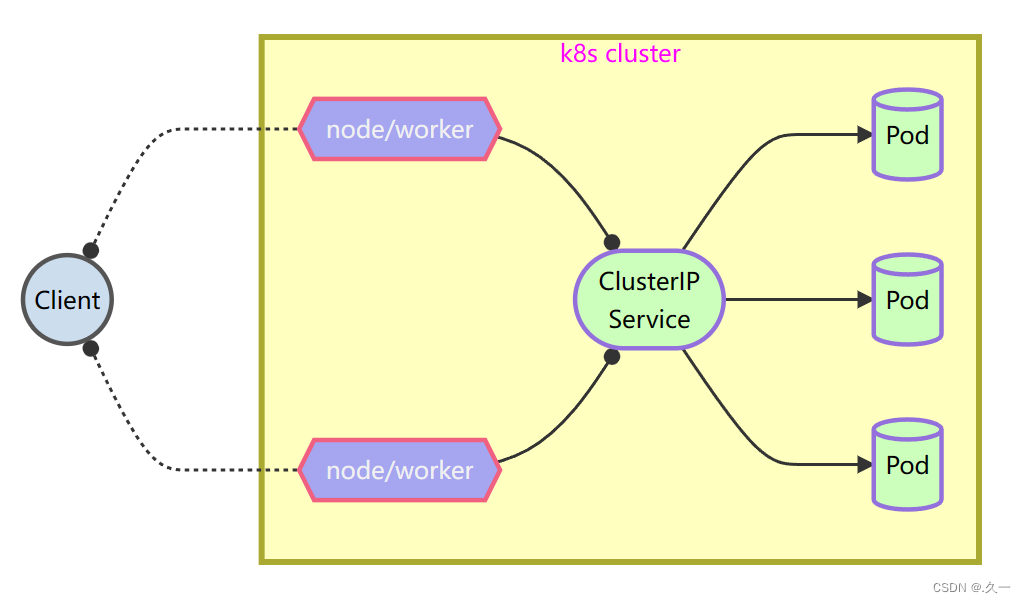
对外发布服务
- [root@master ~]# cp -a mysvc.yaml mysvc1.yaml
- [root@master ~]# vim mysvc1.yaml
- ---
- kind: Service
- apiVersion: v1
- metadata:
- name: mysvc1
- spec:
- type: NodePort # 服务类型
- selector:
- app: web
- ports:
- - protocol: TCP
- port: 80
- nodePort: 30080 # 映射端口号
- targetPort: myhttp
- [root@master ~]# kubectl apply -f mysvc1.yaml
- service/mysvc configured
- [root@master ~]# kubectl get service
- NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
- kubernetes ClusterIP 10.245.0.1 <none> 443/TCP 5d18h
- mysvc ClusterIP 10.245.1.80 <none> 80/TCP 17m
- mysvc1 NodePort 10.245.1.88 <none> 80:30080/TCP 7s
- [root@master ~]# curl http://node-0001:30080
- Welcome to The Apache.
- [root@master ~]# curl http://node-0002:30080
- Welcome to The Apache.
- [root@master ~]# curl http://node-0003:30080
- Welcome to The Apache.
- [root@master ~]# curl http://node-0004:30080
- Welcome to The Apache.
- [root@master ~]# curl http://node-0005:30080
- Welcome to The Apache.
五 Ingress 服务
1 概述
Ingress 公开从集群外部到集群内服务的 HTTP 和 HTTPS路由。流量路由由 Ingress 资源上定义的规则控制。
Ingress 控制器通常由负载均衡器来实现 (Nginx、HAProxy)

2 安装控制器
安装Ingress 控制器
- Ingress 服务由(规则 + 控制器)组成
- 规则负责制定策略,控制器负责执行
- 如果没有控制器,单独设置规则无效
获取控制器镜像及资源文件的地址: https://github.com/kubernetes/ingress-nginx
- # 导入镜像到私有仓库
- [root@master ~]# cd plugins/ingress
- [root@master ingress]# docker load -i ingress.tar.xz
- [root@master ingress]# docker images|while read i t _;do
- [[ "${t}" == "TAG" ]] && continue
- [[ "${i}" =~ ^"harbor:443/".+ ]] && continue
- docker tag ${i}:${t} harbor:443/plugins/${i##*/}:${t}
- docker push harbor:443/plugins/${i##*/}:${t}
- docker rmi ${i}:${t} harbor:443/plugins/${i##*/}:${t}
- done
- # 安装控制器
- [root@master ingress]# sed -ri 's,^(\s*image: )(.*/)?(.+)@.*,\1harbor:443/plugins/\3,' deploy.yaml
- 458: image: harbor:443/plugins/controller:v1.5.1
- 565: image: harbor:443/plugins/kube-webhook-certgen:v20220916-gd32f8c343
- 614: image: harbor:443/plugins/kube-webhook-certgen:v20220916-gd32f8c343
- [root@master ingress]# kubectl apply -f deploy.yaml
- # 通过标签指定在那台机器上发布应用
- [root@master ingress]# kubectl label nodes node-0001 ingress-ready="true"
- node/node-0001 labeled
- [root@master ingress]# kubectl -n ingress-nginx get pods
- NAME READY STATUS RESTARTS AGE
- ingress-nginx-admission-create--1-lm52c 0/1 Completed 0 29s
- ingress-nginx-admission-patch--1-sj2lz 0/1 Completed 0 29s
- ingress-nginx-controller-5664857866-tql24 1/1 Running 0 29s
3 验证后端服务
- [root@master ~]# kubectl get pods,services
- NAME READY STATUS RESTARTS AGE
- pod/web1 1/1 Running 0 35m
- NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
- service/kubernetes ClusterIP 10.245.0.1 <none> 443/TCP 31h
- service/mysvc ClusterIP 10.245.1.80 <none> 80/TCP 34m
- service/mysvc1 NodePort 10.245.1.88 <none> 80:30080/TCP 8s
- [root@master ~]# curl http://10.245.1.80
- Welcome to The Apache.
4 配置 ingress 规则,对外发布服务
- [root@master ~]# kubectl get ingressclasses.networking.k8s.io
- NAME CONTROLLER PARAMETERS AGE
- nginx k8s.io/ingress-nginx <none> 5m7s
- # 资源对象模板
- [root@master ~]# kubectl create ingress mying --class=nginx --rule=nsd.tedu.cn/*=mysvc:80 --dry-run=client -o yaml
- [root@master ~]# vim mying.yaml
- ---
- kind: Ingress # 资源对象类型
- apiVersion: networking.k8s.io/v1 # 资源对象版本
- metadata: # 元数据
- name: mying # 资源对象名称
- spec: # 资源对象定义
- ingressClassName: nginx # 使用的类的名称
- rules: # ingress 规则定义
- - host: nsd.tedu.cn # 域名定义,没有可以不写
- http: # 协议
- paths: # 访问的路径定义
- - backend: # 后端服务
- service: # 服务声明
- name: mysvc # 服务名称
- port: # 端口号声明
- number: 80 # 访问服务的端口号
- path: / # 访问的 url 路径
- pathType: Prefix # 路径的类型,Exact、Prefix
- # 发布服务
- [root@master ~]# kubectl apply -f mying.yaml
- ingress.networking.k8s.io/mying created
- [root@master ~]# kubectl get ingress
- NAME CLASS HOSTS ADDRESS PORTS AGE
- mying nginx nsd.tedu.cn 192.168.1.51 80 70s
- # 访问验证
- [root@master ~]# curl -H "Host: nsd.tedu.cn" http://192.168.1.51
- Welcome to The Apache.
六 web管理插件
Dashboard
<1> 概述
Dashboard 是基于网页的 Kubernetes 用户界面
Dashboard 同时展示了 Kubernetes集群中的资源状态信息和所有报错信息
你可以使用 Dashboard 将应用部署到集群中,也可以对容器应用排错,还能管理集群资源。例如,你可以对应用弹性伸缩、发起滚动升级、重启等等
Dashboard 官网地址:https://github.com/ kubernetes/dashboard
<2> 安装Dashboard
- [root@master ~]# cd plugins/dashboard
- [root@master dashboard]# docker load -i dashboard.tar.xz
- [root@master dashboard]# docker images|while read i t _;do
- [[ "${t}" == "TAG" ]] && continue
- [[ "${i}" =~ ^"harbor:443/".+ ]] && continue
- docker tag ${i}:${t} harbor:443/plugins/${i##*/}:${t}
- docker push harbor:443/plugins/${i##*/}:${t}
- docker rmi ${i}:${t} harbor:443/plugins/${i##*/}:${t}
- done
- [root@master dashboard]# sed -ri 's,^(\s*image: )(.*/)?(.+),\1harbor:443/plugins/\3,' recommended.yaml
- 193: image: harbor:443/plugins/dashboard:v2.7.0
- 278: image: harbor:443/plugins/metrics-scraper:v1.0.8
- [root@master dashboard]# kubectl apply -f recommended.yaml
- [root@master dashboard]# kubectl -n kubernetes-dashboard get pods
- NAME READY STATUS RESTARTS AGE
- dashboard-metrics-scraper-66f6f56b59-b42ng 1/1 Running 0 67s
- kubernetes-dashboard-65ff57f4cf-lwtsk 1/1 Running 0 67s
<3> 发布Dashboard服务
- # 查看服务状态
- [root@master dashboard]# kubectl -n kubernetes-dashboard get service
- NAME TYPE CLUSTER-IP PORT(S) AGE
- dashboard-metrics-scraper ClusterIP 10.245.205.236 8000/TCP 1m50s
- kubernetes-dashboard ClusterIP 10.245.215.40 443/TCP 1m51s
- # 获取服务资源对象文件
- [root@master dashboard]# sed -n '30,45p' recommended.yaml >dashboard-svc.yaml
- [root@master dashboard]# vim dashboard-svc.yaml
- ---
- kind: Service
- apiVersion: v1
- metadata:
- labels:
- k8s-app: kubernetes-dashboard
- name: kubernetes-dashboard
- namespace: kubernetes-dashboard
- spec:
- type: NodePort
- ports:
- - port: 443
- nodePort: 30443
- targetPort: 8443
- selector:
- k8s-app: kubernetes-dashboard
- [root@master dashboard]# kubectl apply -f dashboard-svc.yaml
- service/kubernetes-dashboard configured
- [root@master dashboard]# kubectl -n kubernetes-dashboard get service
- NAME TYPE CLUSTER-IP PORT(S) AGE
- dashboard-metrics-scraper ClusterIP 10.245.205.236 8000/TCP 5m50s
- kubernetes-dashboard NodePort 10.245.215.40 443:30443/TCP 5m51s
- 通过浏览器访问 Dashboard 登录页面

七 服务账号与权限
1 用户概述
<1> 用户认证
所有 Kubernetes 集群都有两类用户:由 Kubernetes 管理的服务账号和普通用户。
普通用户是以证书或秘钥形式签发,主要用途是认证和鉴权集群中并不包含用来代表普通用户账号的对象,普通用户的信息无法调用和查询。
服务账号是 Kubernetes API 所管理的用户。它们被绑定到特定的名字空间,与一组 Seret 凭据相关联,供 Pod 调用以获得相应的授权。
<2> 创建 ServiceAccount 服务账号
- # 资源对象模板
- [root@master ~]# kubectl -n kubernetes-dashboard create serviceaccount kube-admin --dry-run=client -o yaml
- [root@master ~]# vim admin-user.yaml
- ---
- kind: ServiceAccount
- apiVersion: v1 # 版本
- metadata: # 资源对象类型
- name: kube-admin # ServiceAccount
- namespace: kubernetes-dashboard # 名称空间
- [root@master ~]# kubectl apply -f admin-user.yaml
- serviceaccount/kube-admin created
- [root@master ~]# kubectl -n kubernetes-dashboard get serviceaccounts
- NAME SECRETS AGE
- default 0 16m
- kube-admin 0 11s
- kubernetes-dashboard 0 16m
<3> 获取用户token
- [root@master ~]# kubectl -n kubernetes-dashboard create token kube-admin

2 权限管理
<1> 角色与鉴权
如果想访问和管理 kubernetes 集群,就要对身份以及权限做验证,kubernetes 支持的鉴权模块有 Node、RBAC、ABAC、Webhook AP
- Node:一种特殊用途的鉴权模式,专门对 kubelet 发出的请求进行鉴权。
- RBAC:是一种基于组织中用户的角色来控制资源使用的方法
- ABAC:基于属性的访问控制,是一种通过将用户属性与权限组合在一起像用户授权的方法
- Webhook:是一个HTTP回调
<2> 普通角色授权
- # 查询当前集群使用的鉴权方法
- [root@master ~]# kubectl cluster-info dump |grep authorization-mode
- "--authorization-mode=Node,RBAC",
- # 资源对象模板
- [root@master ~]# kubectl -n default create role myrole --resource=pods --verb=get,list --dry-run=client -o yaml
- [root@master ~]# kubectl -n default create rolebinding kube-admin-role --role=myrole --serviceaccount=kubernetes-dashboard:kube-admin --dry-run=client -o yaml
- [root@master ~]# vim myrole.yaml
- ---
- kind: Role
- apiVersion: rbac.authorization.k8s.io/v1
- metadata:
- name: myrole
- namespace: default
- rules:
- - apiGroups:
- - ""
- resources:
- - pods
- verbs:
- - get
- - list
- ---
- kind: RoleBinding
- apiVersion: rbac.authorization.k8s.io/v1
- metadata:
- name: kube-admin-role # 授权名称
- namespace: default
- roleRef: # 关联权限
- apiGroup: rbac.authorization.k8s.io # 角色对象组
- kind: Role # 角色对象
- name: myrole # 角色名称
- subjects: # 授权信息
- - kind: ServiceAccount # 账户资源对象
- name: kube-admin # 账户名称
- namespace: kubernetes-dashboard # 账户所在的名称空间
- [root@master ~]# kubectl apply -f myrole.yaml
- role.rbac.authorization.k8s.io/myrole created
- rolebinding.rbac.authorization.k8s.io/kube-admin-role created
- [root@master ~]# kubectl delete -f myrole.yaml
- role.rbac.authorization.k8s.io "myrole" deleted
- rolebinding.rbac.authorization.k8s.io "kube-admin-role" deleted
<3> RBAC 授权
RBAC 声明了四种 Kubernetes 对象:
- Role:用来在某一个名称空间内创建授权角色,创建 Role时,必须指定所属的名字空间的名
- ClusterRole:可以和 Role 相同完成授权。但属于集群范围,对所有名称空间有效。
- RoleBinding:是将角色中定义的权限赋予一个或者一组用户,可以使用 Role或ClusterRole 完成授权。
- ClusterRoleBinding 在集群范围执行授权,对所有名称空间有效,只能使用 clusterRole 完成授权
<4> 资源对象角色与作用域

<5> 资源对象权限

<6> 自定义权限
- ---
- kind: Role
- apiVersion: rbac.authorization.k8s.io/v1
- metadata:
- name: myrole # 角色名称
- namespace: default
- rules: # 规则
- - apiGroups: # 资源对象所属组信息
- - "" # 分组信息
- resources: # 要设置权限的资源对象
- - pods # 授权资源对象名称
- verbs: # 权限设置
- - get # 权限
- - list # 权限
<7> 集群管理员权限
- [root@master ~]# kubectl get clusterrole
- NAME CREATED AT
- admin 2022-06-24T08:11:17Z
- cluster-admin 2022-06-24T08:11:17Z
- ... ...
- # 资源对象模板
- [root@master ~]# kubectl create clusterrolebinding kube-admin-role --clusterrole=cluster-admin --serviceaccount=kubernetes-dashboard:kube-admin --dry-run=client -o yaml
- [root@master ~]# vim admin-user.yaml
- ---
- kind: ServiceAccount
- apiVersion: v1
- metadata:
- name: kube-admin
- namespace: kubernetes-dashboard
- ---
- kind: ClusterRoleBinding
- apiVersion: rbac.authorization.k8s.io/v1
- metadata:
- name: kube-admin-role
- roleRef:
- apiGroup: rbac.authorization.k8s.io
- kind: ClusterRole
- name: cluster-admin
- subjects:
- - kind: ServiceAccount
- name: kube-admin
- namespace: kubernetes-dashboard
- [root@master ~]# kubectl apply -f admin-user.yaml
- serviceaccount/kube-admin unchanged
- clusterrolebinding.rbac.authorization.k8s.io/kube-admin-role created
-
相关阅读:
vue3源码分析——实现element属性更新,child更新
Clusterpedia 使用心得
云化Web IDE,在线开发新模式
怎么从0到1实现一个PHP框架?
ES 客户端 RestHighLevelClient Connection reset by peer 亲测有效 2022-11-05
Linux下根目录都包含什么? 每个文件什么作用?
kubectl 速查手册
【脑机接口论文与代码】 基于自适应FBCCA的脑机接口控制机械臂
《Unix 网络编程》11:名字和地址转换
EvilJS 的 Golang 实现
- 原文地址:https://blog.csdn.net/2301_79227925/article/details/132745473